In this post I will summarize my notes from this article and this video. My intent is to understand the basic functionality and operation of the maritime CAN bus NMEA 2000 and understand the basic vulnerabilities of this system.
I believe that the NMEA 2000 is worth notice as at the moment is lacking basic security yet controls important onboard systems and may facilitate lateral access to other networks.
I hope to highlight the existence of maritime unique systems that are vulnerable to conventional cyber attacks.
Notes
The Controller Area Network (CAN) bus was developed in the early 1980s and has been in wide use for intra-vehicular communication since its initial introduction 30 years ago, primarily for automobiles and other land vehicles.
Unlike the point-to-point and multidrop serial protocols of the day, the CAN bus is a broadcast bus where any device can transmit when it is ready and does not have to wait to be polled by some master station; the CAN bus standard refers to this as a multimaster protocol because all devices are, essentially, peers.
In terms of the Open Systems Interconnection (OSI) reference model, the CAN bus standard provides physical and data link layer (layer 1 and 2) services. Any suitable higher layer protocol can be designed or adapted to run over the CAN bus.
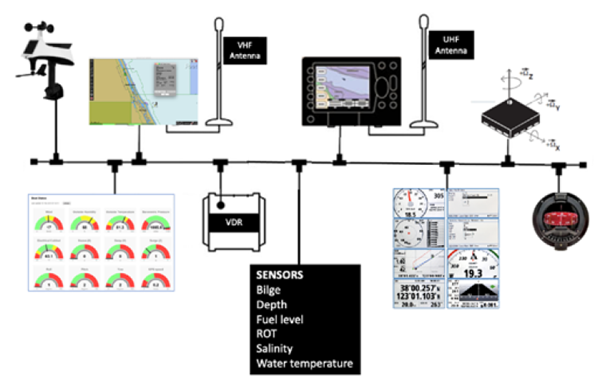
In maritime vessels the CAN bus protocol is called NMEA 2000 and is used to interconnect such equipment as the wind speed/wind direction/air temperature sensors, Automatic Identification System (AIS), Global Navigation Satellite System
(GNSS), gyroscope, compass, navigation display, a large variety of ship status sensors, voyage data recorder (VDR), and ship state dashboard display.
NMEA 2000 does not incorporate any native security features pertaining to confidentiality, authentication, authorization, or non-repudiation.
NMEA 2000 is vulnerable to Denial of Service, Spoofing, Packet Sniffing and Replay/Man-in-the-Middle
Denial of Service
We posit that NMEA 2000 is highly vulnerable to Denial of Service attacks due to its
low-bandwidth design.
Our review of the protocol further identified that NMEA 2000 is vulnerable to spoofing attacks [31], where the Parameter Group Number (PGN) used to identify the sending node is copied and used by a malicious device. This imposes an added problem because in NMEA 2000, the PGN is also used to indicate the priority of the message.
NMEA 2000 operates on a single broadcast domain. All nodes on the message channel (similar to a bus on CAN Bus) receive all messages [32,33]. It is the responsibility of the nodes to discern which messages to discard as unneeded. We suggest that this make passively sniffing messages a trivial task, assuming physical access is possible.
Replay/Man-in-the-Middle
Because NMEA 2000 operates on a broadcast principle, an inline device could be placed between the target node and the rest of the channel (bus). This malicious inline device would be able to pass along messages from either the target node or the rest of the channel in either direction. We have identified a layer of protection in that NMEA 2000 contains a 15-bit Cyclic Redundancy Check (CRC) [5] (inherited from CAN bus). However, this is designed to detect transmission errors, rather than deliberate tampering as CRC is not considered to be cryptographically secure.
Related articles:
Tthe CAN Bus in the Maritime Environmen (PDF)
Marine Network Protocols and Security Risks
Related videos:
openBridge: NMEA 2000 for Everyone – Constantine Macris DEF CON 29
Stephan Gerling – Hacking Yachts Remotely via Satcom or Maritime Internet Router
